Microsoft Azure and SonicWALL STS – Part 1 – Configure Azure Resource Group
Microsoft Azure and SonicWALL STS – Part 2 – Configure SonicWALL OS VPN policy
Microsoft Azure and SonicWALL STS – Part 3 – Configure VPN policies and Routing
Extending the on-premises infrastructure to Azure, the obligatory need is to create site-to-site VPN to access resources in both side. This article shows you the steps of setting up Azure Site-to-Site VPN with SonicWALL OS including the steps required to be carried out in planning phase, execution phase in Azure and in On-premises configuration phase. Here, we will be using Resource Group Deployment model in Azure instead of Classic Deployment Model.
Planning Phase:
- In the planning phase, we should first check the compatibility of the VPN device which will be part of the configuration. In this connection, the on-premises network get connected with Azure Virtual Network over an IPsec/IKE (IKEv1 & IKEv2) VPN tunnel.
- The compatible VPN devices are specified here in MS article https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices
- We must be ensured that you have a static public IP address pointed to the on-premise VPN device. The on-premise LAN subnet (The IP class and subnet must not be similar as VNet at Azure end)
- Subsequent Azure subscriptions requirements.
- A person from network team who is aware of firewall rules and Static/Dynamic routing and ability to configure the hardware and software configuration of the VPN Device.
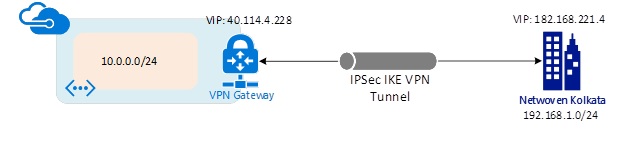
Logical Topology:
Implementation Steps:
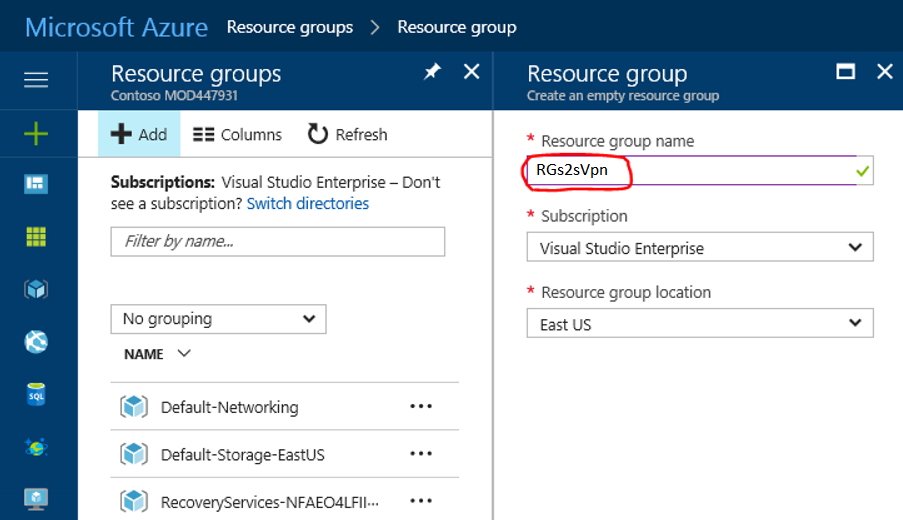
- Resource Group: –
- Login to Azure Portal>>Navigate to “Resource Group” at left site of window>>Click “Add”.
- Put the Resource Group name>> Select the “Subscription” and “Location”>>Click “OK”.
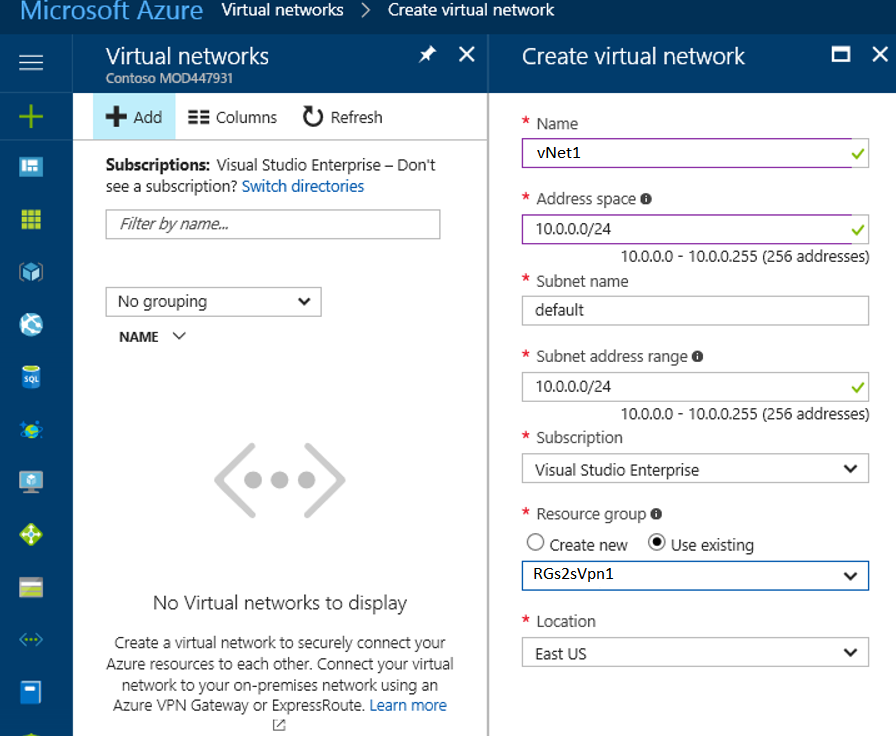
- Create Virtual Network –
- Click New (+) at the top left side corner of the portal >> Search in the marketplace>>type ‘Virtual Network’. Click on “Add” to create a new “Virtual Network”.
- Put the name of the virtual network>>then select the “Subnet”. We may use any custom subnet.
- Select the “Resource Group” which we have created before.
- Create Gateway Subnet
- In the Virtual Network, we need to add the “Gateway Subnet”. “172.16.1.0/27”
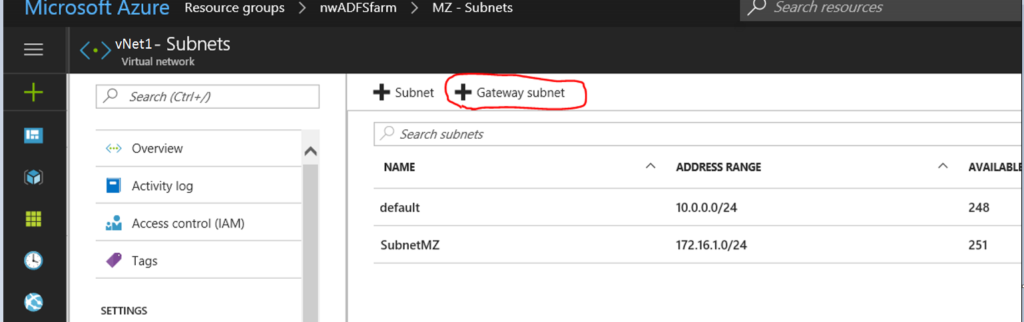
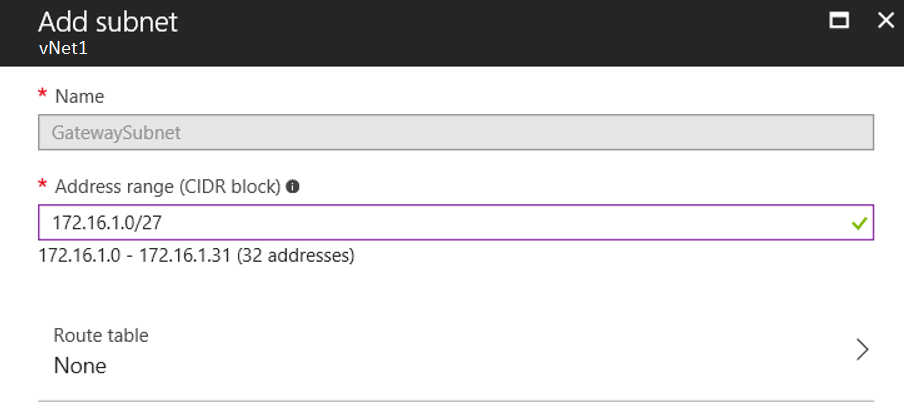
- Create Virtual Network Gateway
- In the search market place, search with the key words “Virtual Network Gateway” then select from the list and click on “Create”.
- Here, we need to first assign a identical name relating to all resources falling under a acceptable naming convention. Then proceed to the area where we need to map the virtual network that would be the part of our configurations.
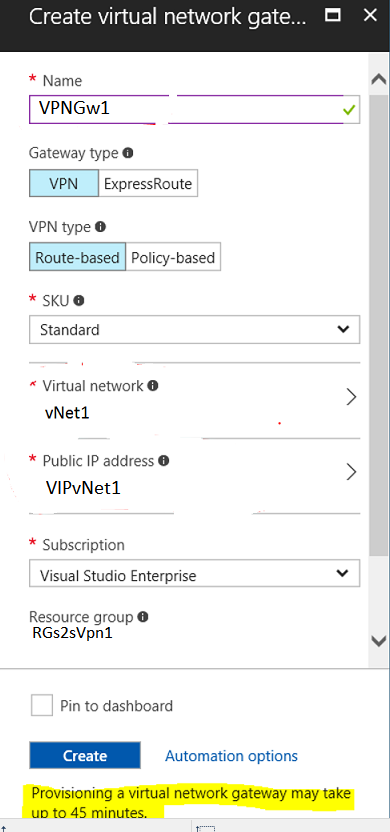
Then we need to generate the public IP for the Gateway if we do not already have one. The resource group should be chosen from the existing resource group. Caution: Ensure that you choose the correct resource group in which you are creating the other associated resources falling in the same Azure location if your Azure tenant already has multiple resource groups. This is important because the STS will only work if all your resources are in the same azure region under a single resource group. It will take couple of minutes to provision the public IP’s and its backend association to the VNet Gateway. So please hold on and wait till the process gets over.
- Local Network Gateway
- This area refers to the on-premises network where we will set the network subnet to access the resources of Azure virtual network. We need to keep in mind here we can only add the subnet which has assigned to none of the VNet in Azure.
- Here, in our environment we have two subnets defined in on-premises. One of the subnet (10.0.0.0/16) is similar with the subnet defined in one of the Vnet which would not be added in “Local Gateway”. We have added another subnet “192.168.1.0/24”.
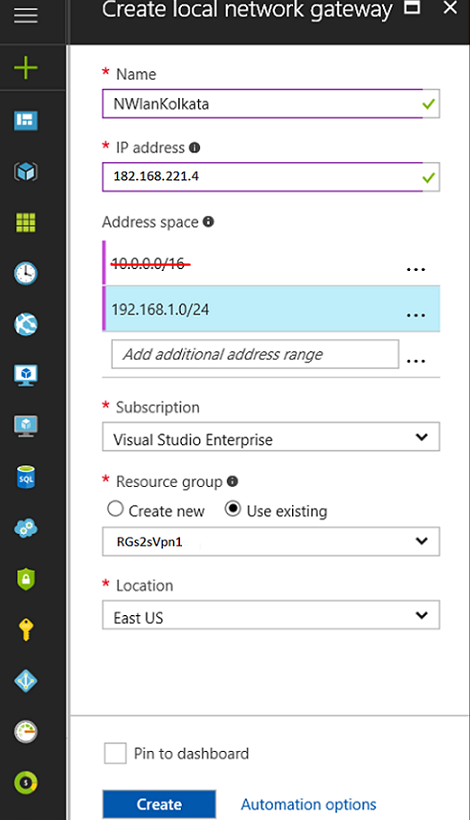
- Configure the on-promises VPN device
- Now the configuration is needed in the on-premises VPN device and thereafter we will be able to add connection and build tunnel with Azure. Here, we have used SonicWALL device as VPN device.
Stay tuned for the next TechTalk, where we will see the configuration steps in SonicWALL device along with the Azure configurations. In addition, we will cover the steps that are needed for Network Security Group (NSG) in Azure and firewall rules in the VPN device.
Upcoming articles:
Microsoft Azure and SonicWALL STS – Part 2 – Configure SonicWALL OS VPN policy
Microsoft Azure and SonicWALL STS – Part 3 – Configure VPN policies and Routing