Sensitive Information Protection with Microsoft Purview
Protect your organization with this in-depth eBook on Microsoft Purview by Netwoven and help secure your organization today!
Protect your organization with this in-depth eBook on Microsoft Purview by Netwoven and help secure your organization today!
Do you know what kinds of sensitive information you have and where it lives? How are you currently securing sensitive data across all your environments and preventing its loss? And how do you manage insider risks? These are all questions today’s businesses need to be asking. More than 80% of decision-makers purchase multiple products to meet compliance and data security needs. However, this approach can be costly, hard to manage—and still leave gaps. A holistic approach to data security is essential. That’s where Microsoft Purview Information Protection can help
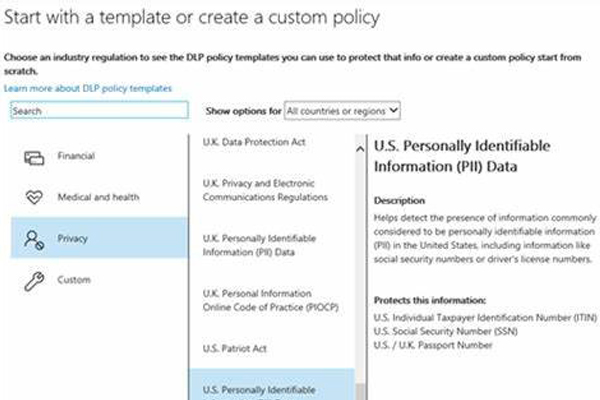
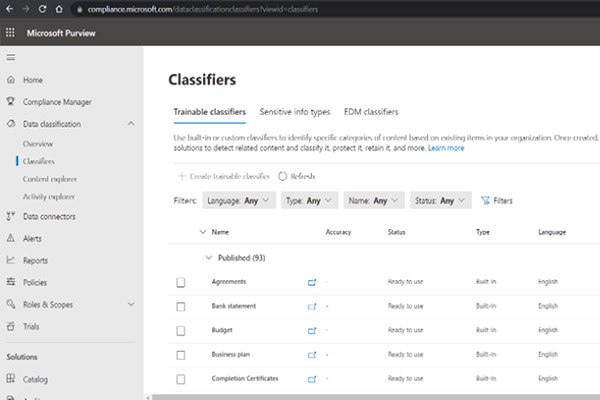
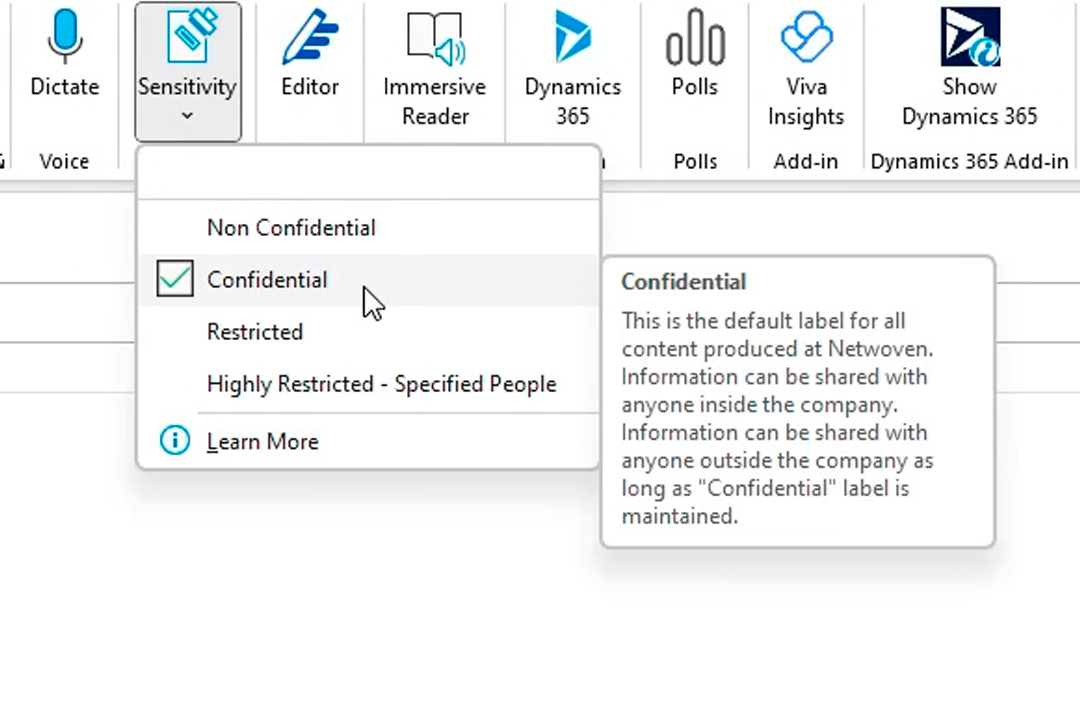
Netwoven is a leading provider of Microsoft Purview Information Protection solutions that help our clients protect their sensitive information and comply with regulatory requirements. With Microsoft Purview, Netwoven can classify, and label sensitive data based on policies and regulations such as GDPR, CCPA, HIPAA, etc.
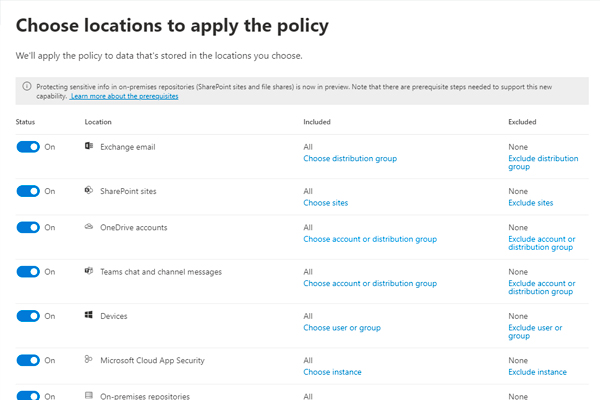
Netwoven works with the clients to understand the requirements, build a data strategy, configure and customize Microsoft Information Protection policies and labels, implement rollout, provide adoption and change management, and support the clients through their journey of becoming a secure organization. Netwoven is an expert in the migration of non-Microsoft data security products like Titus, Seclore, etc. to Microsoft Purview Information Protection.
By integrating Microsoft Purview Information Protection with other Microsoft security and compliance tools, such as Azure Sentinel and Compliance Manager, we can provide our clients with a holistic solution to information protection and compliance.



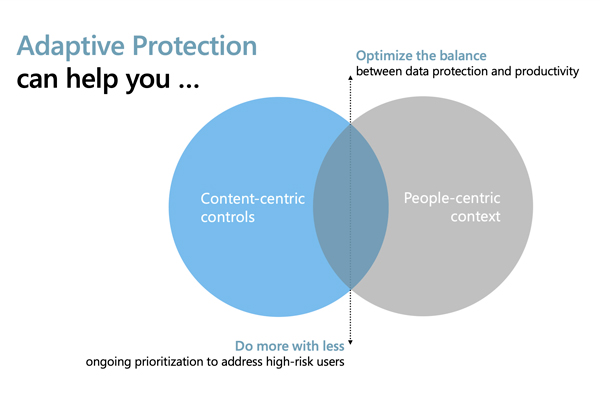


Introduction Microsoft Purview is a comprehensive set of solutions that can help your organization govern, protect, and manage data, wherever it lives. Many solutions come under Microsoft Purview, but we… Continue reading A Guide to Seamlessly Adopting Microsoft Purview for Your Organization
Introduction The semiconductor manufacturing industry is the backbone of the digital global economy. In most cases the data generated in this industry is highly sensitive and if obtained by competitors… Continue reading How Microsoft Purview Facilitates Regulatory Compliance for Semiconductor Manufacturing Industry
In today’s fast-paced digital landscape, staying ahead of cybersecurity threats is paramount. Microsoft’s suite of security solutions plays a pivotal role in safeguarding your organization. To help you make the… Continue reading Top 7 Questions on How to Protect Your Business Data
Introduction: This is the third blog in a series about Microsoft Information Protection best practices that began with our first two blogs. Since Microsoft Purview is continually being upgraded and… Continue reading Microsoft 365 Data Governance: Microsoft Purview Security Best Practices
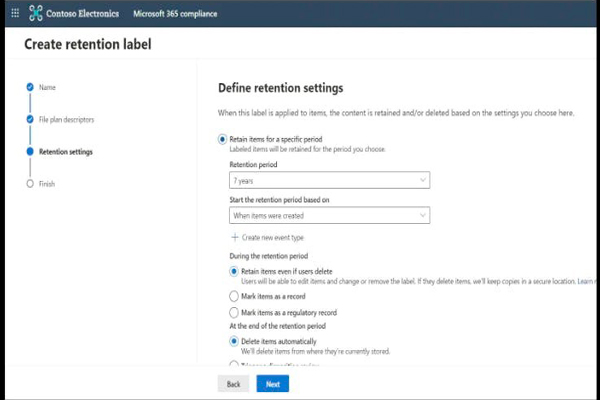
Microsoft Purview is a comprehensive portfolio of products spanning data governance, information protection, risk management, and compliance solutions. Microsoft Purview helps organizations to: Below table shows the different capabilities available… Continue reading 8 Tips to Successfully Deploy A Microsoft Purview Compliance Project

Prefer to call?1-877-638-9683
Drop us a mailinfo@netwoven.com
Find out how we can help you with your organization’s digital transformation journey.